March 03, 2025
Our analyst team shares a few articles each week in our email newsletter which goes every Thursday. Make sure to register! This blog highlights those articles in order of what was the most popular in our newsletter – what our readers found the most intriguing. Stay tuned for a recap every month. We hope sharing these resources and news articles emphasizes the importance of cybersecurity and sheds light on the latest in threat intelligence.
1. Dutch Police seizes 127 XHost servers, dismantles bulletproof hoster – Bleeping Computer
Clik here to view.

In a February 11 press release, the U.K. government—along with the U.S. and Australia—announced the imposition of new sanctions targeting the Russian cyber entity “Zservers.” A day after the announcement of sanctions, Dutch Police dismantled Zservers/XHost and seized 127 associated servers. As noted in the U.K.’s press release, the Russia-based bulletproof hosting (BPH) services provider was a “key component of the Russian cybercrime supply chain” and was responsible for “facilitating crippling ransomware attacks globally.” Zservers notably provided “essential attack infrastructure” for the notorious LockBit ransomware gang. Read full article.
2. Russian military hackers deploy malicious Windows activators in Ukraine – Bleeping Computer
The Russian hacker group Sandworm (also known as “Seashell Blizzard”) has been observed targeting Windows users in Ukraine with malicious Windows activators. The cyber-espionage group—which has been linked to Military Unit 74455 of the GRU—has specifically deployed trojanized Microsoft Key Management Service (KMS) activators, fake Windows updates, and DarkCrystal RAT malware via a BACKORDER loader. It is believed that the attacks began in late 2023 and aim to “collect sensitive information from infected computers and send it to attacker-controlled servers.” Article here.
3. Meta Confirms Zero-Click WhatsApp Spyware Attack Targeting 90 Journalists, Activists – The Hacker News
Clik here to view.

Meta has confirmed that WhatsApp users have been targeted in a global spyware campaign. The campaign involved the use of spyware developed by the Israeli company Paragon Solutions, which has since received a cease and desist letter from Meta following the incident. Nearly 100 WhatsApp users were impacted by the campaign, most of whom were journalists or “other members of civil society.” As noted by The Guardian, WhatsApp shared that it had “’high confidence’ that the 90 users in question had been targeted and ‘possibly compromised.” Read more here.
4. Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign – The Hacker News
Clik here to view.
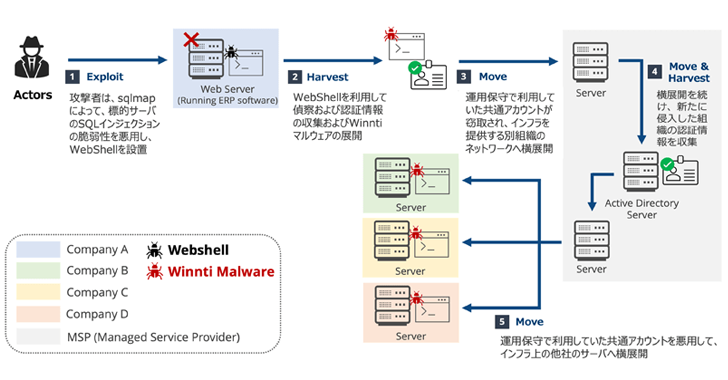
Researchers at the Japanese cybersecurity firm LAC have identified a new cyberespionage campaign dubbed “RevivalStone” targeting Japanese companies. The activity has been tied to the China-linked advanced persistent threat (APT) group Winnti (also known as APT41). The campaign took place in March 2024 and specifically targeted companies in the manufacturing, materials, and energy sectors. According to the researchers, the campaign uses an updated version of Winnti malware with new capabilities. Read here.
5. E.U. Sanctions Three GRU Officers For Cyberattacks Against Estonia – The Hacker News
On January 27, the Council of the European Union announced the sanctioning of three GRU officers for their role in cyberattacks against Estonia’s government in 2020. As noted in the Council’s press release, the three Russian nationals—Nikolay Korchagin, Vitaly Shevchenko, and Yuriy Denisov—gained “unauthorized access to classified information and sensitive data stored within several government ministries […] leading to the theft of thousands of confidential documents.” Learn more.
6. Spain arrests suspected hacker of US and Spanish military agencies – Bleeping Computer
Spain’s Guardia Civil and Policía Nacional have arrested “Natohub,” a notorious 18-year-old hacker in Alicante who allegedly conducted more than 40 cyberattacks against Spanish and international organizations, “including the Guardia Civil, the Ministry of Defense, NATO, the US Army, and various universities.” According to the Policía Nacional’s official press release, the suspect utilized three different pseudonyms while targeting international government organizations and accessed databases containing personal information belonging to employees and clients, as well as internal documents. Read full article.
7. North Korean Hackers Exploit PowerShell Trick to Hijack Devices in New Cyberattack – The Hacker News
Clik here to view.

The North Korean hacker group Kimusky (also known as Velvet Chollima and Emerald Sleet) has been observed using a new tactic which involves tricking its targets into “running PowerShell as an administrator and then pasting and running code provided by the threat actor.” As noted by the Microsoft Threat Intelligence team, the threat actor masquerades as a South Korean government official and attempts to build rapport with the victim before ultimately sending a spear phishing email. Read full article.
8. CISA and FBI: Ghost ransomware breached orgs in 70 countries – Bleeping Computer
Clik here to view.

On February 19, the Cybersecurity & Infrastructure Agency (CISA), Federal Bureau of Investigation (FBI), and Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint advisory detailing indicators of compromise (IOCs) and tactics, techniques, and procedures (TTPs) associated with Ghost (Cring) Ransomware. Since 2021, threat actors utilizing Ghost ransomware have targeted organizations in more than 70 countries. Victims have included organizations in a variety of sectors, including critical infrastructure, education, and healthcare. Learn more.
Make sure to register for our weekly newsletter to get access to what our analysts are reading on a weekly basis.
The post Threat Intelligence RoundUp: February appeared first on DarkOwl, LLC.