March 13, 2025
How many Wi-Fi networks has your smartphone, laptop, or IoT device connected to over its lifetime? If your device is more than a few months old, the number could be surprisingly high. By default, devices typically store Wi-Fi access points and automatically attempt to rejoin them – even when they are not in range of the access point. As a result, they continuously broadcast a list of the networks they’re trying to connect to. This constant “auto-join” behavior may inadvertently reveal your whereabouts, commonly visited locations, and likely your home. In the wake of the recent assassination of a major healthcare executive, executive protection and security teams need to stay technologically savvy to potential privacy leaks—any technology that can be used to discover an individual’s location becomes a serious concern.
As a result of the Edward Snowden leaks, a Canadian intelligence technique, used by the Communications Security Establishment Canada (CSEC), was exposed to the public with details reported in 2014. Leaked documents from the CSEC confirm that tracking individuals via their Wi-Fi and IP metadata is far from theoretical. By starting with a known “seed” access point (often at airports or hotels), government officials identified devices connected to hotspots and traced these devices forward and backward in time through other networks. This so-called “travel node” approach leverages big-data analytics to build detailed movement profiles, revealing not only routine routes (like daily commutes) but also one-off visits to coffee shops, internet cafés, or conference centers—demonstrating just how valuable Wi-Fi metadata can be for pinpointing a person’s location and habits.
Shielding your privacy from sophisticated nation-state intelligence operations may or may not be your primary concern regarding cyber privacy. However, the technique of tracking, fingerprinting, and identifying individuals based on Wi-Fi metadata isn’t limited to nation-state actors. Open-source tools like AiroDump-ng, AirGraph-ng, and websites such as Wigle.net can also be used by less-sophisticated adversaries to potentially locate persons of interest and their routine habits.
Before we dig in, lets better understand how MAC addresses work and why they are important.
MAC Addressing
Every device that connects to a network is assigned a unique MAC address if it doesn’t already have a permanent, manufacturer-assigned one. Depending on the device, the MAC address might be completely random, partially random, permanently set once assigned, regularly reset, or permanently assigned from the factory. The important thing to consider is that some manufacturers don’t randomize your MAC address, which makes it much easier to identify you electronically.
A MAC address is typically represented as six segments of hexadecimal values, for example: 44:38:39:FF:EF:57. The first three segments (44:38:39) often represent the Organizationally Unique Identifier (OUI) associated with the device vendor—in this example, Cumulus Networks, Inc. Several MAC address lookup websites can provide further details about the vendor based on the OUI.
This is noteworthy because the MAC address is not hidden and can be captured by anyone within range of your access point, even without connecting to your network.
Below is a screenshot showing an example MAC address and its vendor details obtained by searching the OUI on an online lookup tool.
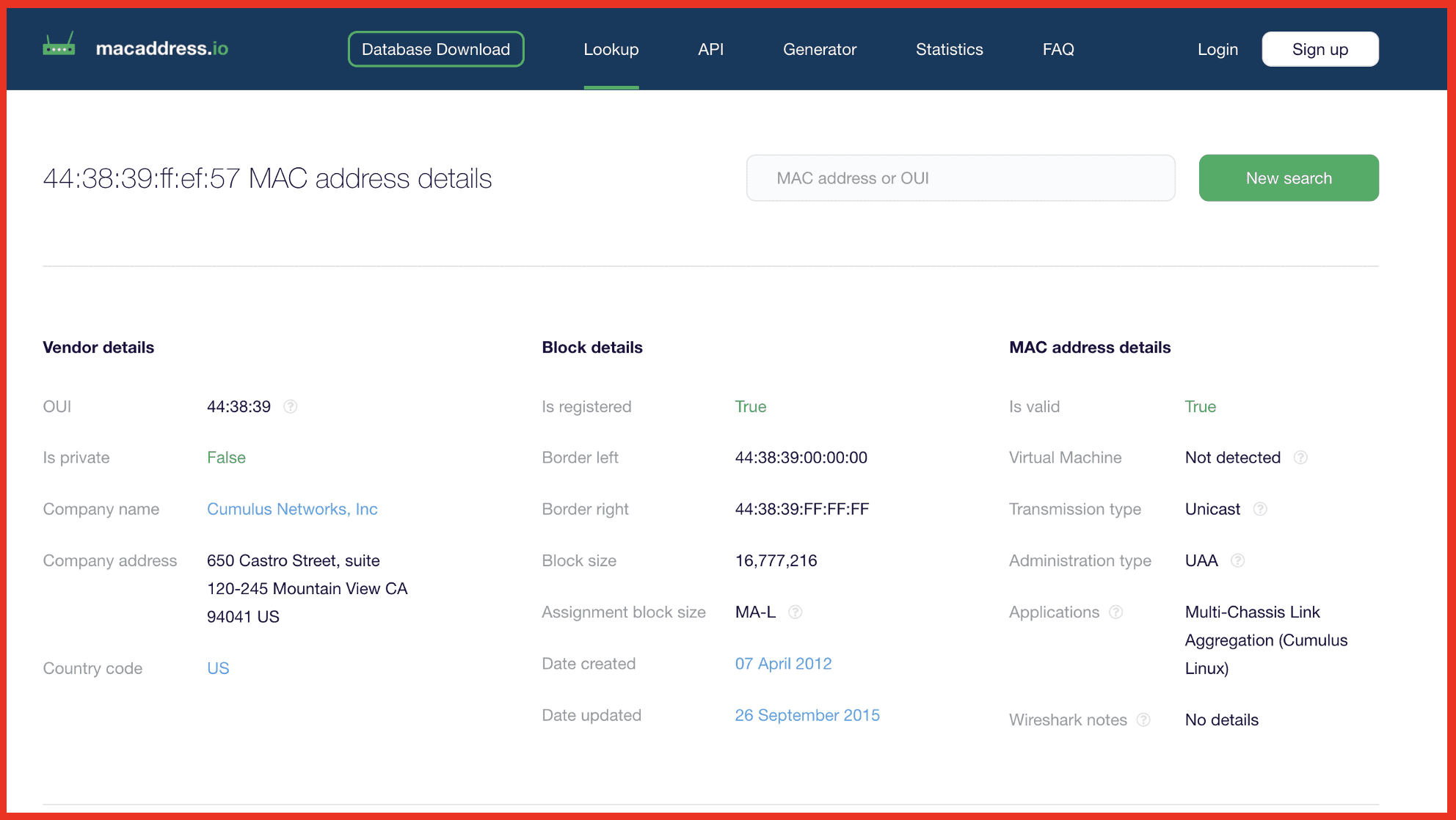
You can already see how devices that constantly broadcast their presence might leak sensitive information, but let’s take this a step further.
Tools like AiroDump-ng allow even unsophisticated actors to sniff Wi-Fi-enabled devices whether connected or unconnected to a network. Once an actor collects data from an area of interest, it can be visualized using another tool called AirGraph-ng. Both tools are free and come pre-installed in the Kali Linux operating system—a popular OS among cybersecurity professionals, hobbyists and bad actors alike.
AiroDump-ng & AirGraph-ng
Since this blog isn’t a tutorial on how to use AiroDump-ng, let’s focus on the user-friendly output graphs from AirGraph-ng and how they fit into the broader conversation on device fingerprinting and potentially identifying a person’s routine habits. For context, the data we’ll discuss was all collected using AiroDump-ng and visualized with the AirGraph-ng tool.
In the image below, you can see several key details regarding the access points and the clients connected to them. The two green circles represents a Wi-Fi access point, along with its encryption type, the number of connected devices, the MAC address, the OUI, and the ESSID (Wi-Fi name). For each access point, you can view which clients are connected, as well as other related information about the device.
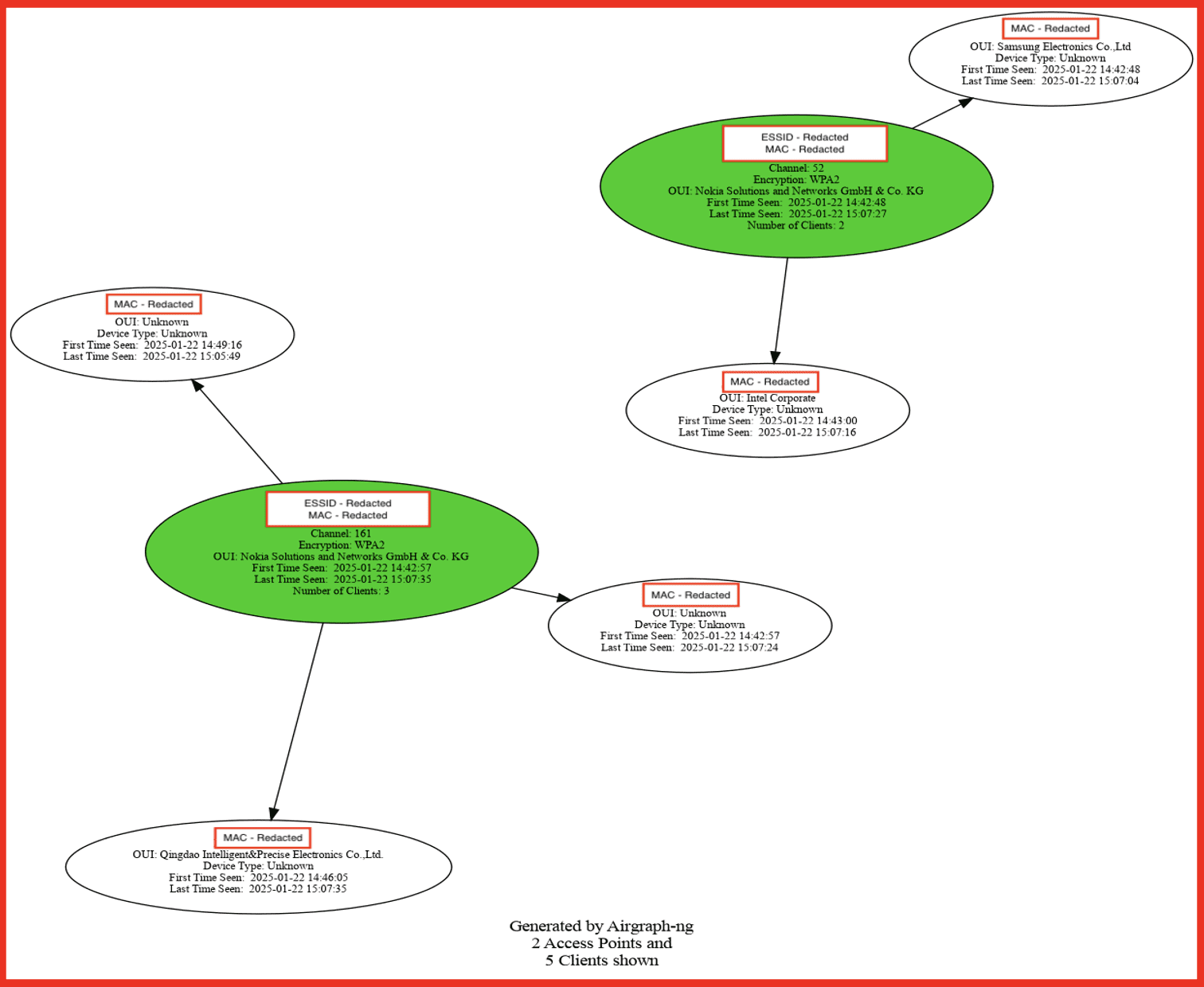
It’s also possible to monitor the access points that clients are attempting to join. As mentioned earlier, Wi-Fi devices are constantly broadcasting a list of networks they’d like to connect to. The image below illustrates this: a cluster of devices probing for connections and networks stored in their settings as “auto-join.” For privacy reasons, non-public access points have been redacted from the image.

It’s also possible to monitor the access points that clients are attempting to join. As mentioned earlier, Wi-Fi devices are constantly broadcasting a list of networks they’d like to connect to. The image below illustrates this: a cluster of devices probing for connections and networks stored in their settings as “auto-join.” For privacy reasons, non-public access points have been redacted from the image.
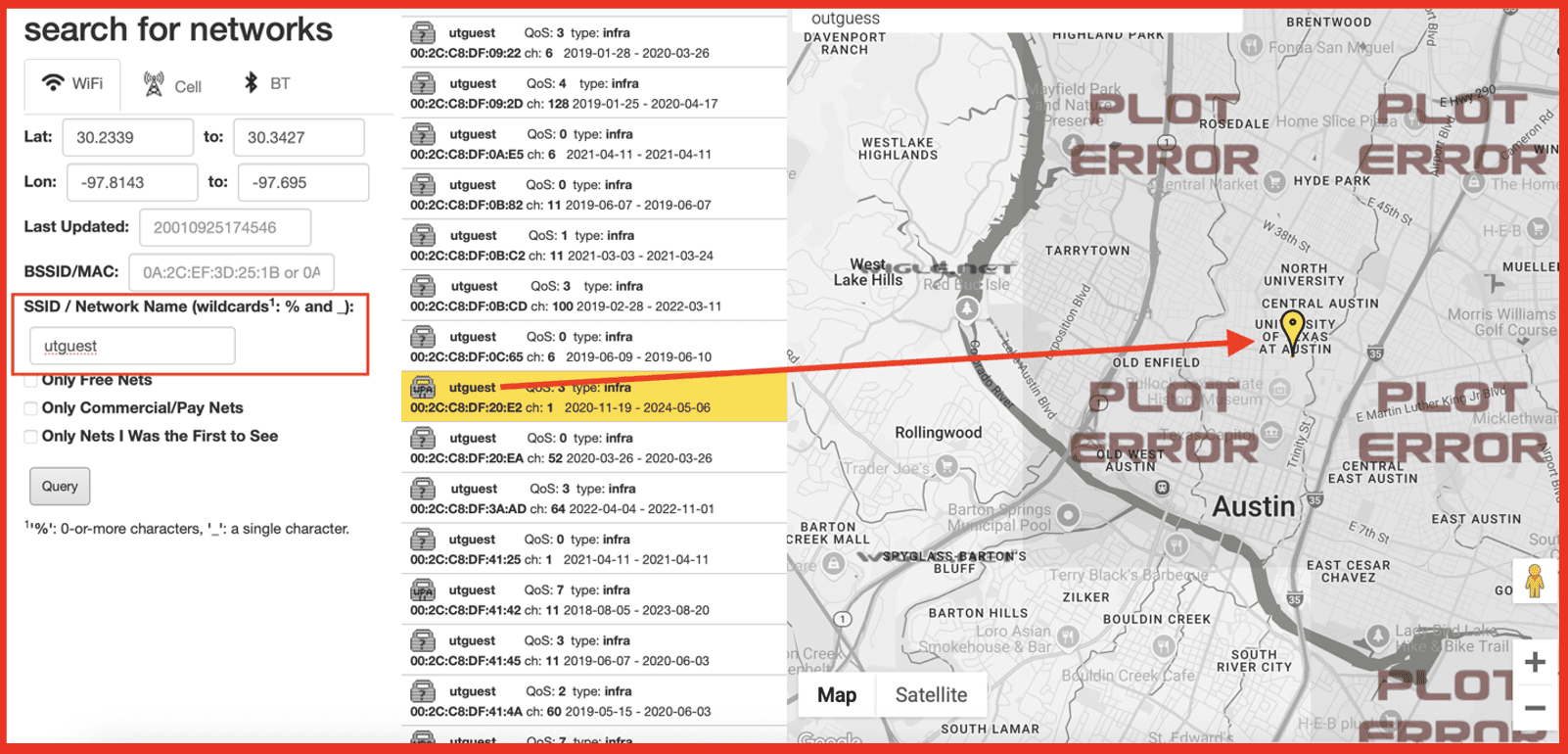
[wiglet.net]
In the center panel, you can see multiple matches for our query, all indicating that this access point is located on The University of Texas at Austin’s downtown campus. Although we chose a public network for our research, you can imagine the privacy implications if this method were used on private networks to build a fingerprint or track someone’s daily routine across multiple access points.
Summary
In this blog, we explored how Wi-Fi metadata can reveal a person’s commonly visited locations by first examining the significance of MAC addresses. MAC addresses—whether permanent or randomly generated—provide identifiable details, including the device vendor’s Organizationally Unique Identifier (OUI). Because they’re broadcast openly, anyone in range of a Wi-Fi access point can easily capture them.
Next, we introduced practical tools like AiroDump-ng, which can sniff Wi-Fi data, and AirGraph-ng, which visualizes the relationships between access points and connected clients. Although these tools are commonly used by cybersecurity professionals, they can also be leveraged by less-sophisticated actors to gather detailed information about nearby networks and devices. Notably, devices often broadcast networks they want to join, including non-public or previously connected networks, further underscoring the privacy risks of Wi-Fi metadata.
We then demonstrated how Wigle.net can take these broadcasted ESSIDs (Wi-Fi names) and provide a geographic location of the associated access points. Our example focused on a public network at the University of Texas at Austin’s downtown campus, illustrating how even publicly visible data can reveal specific locations. The implications grow more serious if similar methods are used against private networks to build a profile of someone’s daily movements or routine.
By being aware of how simple it is to collect and analyze Wi-Fi metadata, individuals and organizations can take proactive steps to safeguard their privacy and minimize the risk of being tracked. Ultimately, these insights emphasize the importance of cyber hygiene—a blend of technological practices (like MAC address randomization and cautious network selection) and informed awareness (knowing what data is visible and how it can be used)—to protect both personal and professional security.
Check our blog on Executive Protection and the Dark Web.
The post How your Wi-Fi Metadata Could be Leaking Your Location – Executive Protection Awareness appeared first on DarkOwl, LLC.